August 25, 2022
Windows KB5012170 is turning out to be one of those patches that is causing a ton of headaches. The biggest one is for those user’s that got the lovely BitLocker Recovery screen but had no idea what their BitLocker recovery key is or where to find it. This happened to my father-in-law’s laptop and unfortunately the recovery key was not listed in his Microsoft account. His laptop was basically ransomwared without the ability to pay the ransom (luckily his son-in-law knows a thing or two about deploying Windows).
The intent of this patch is actually good as it addresses three security vulnerabilities (CVEs) by updating the Secure Boot Forbidden Data (DBX) and blocking these compromised boot loaders. In other words, do not skip it, but rather take a crawl-walk-run approach when deploying it and be sure to test it thoroughly. Microsoft has now acknowledged another issue with this patch where it fails to install with error 0x800F0922. This is now listed on the support article under know issues:
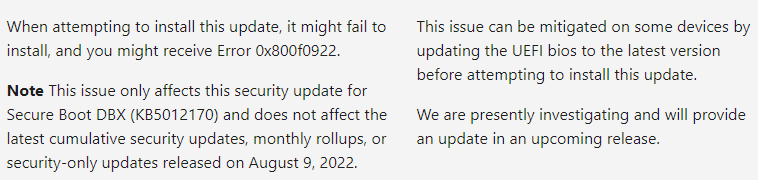
Although not as bad as the BitLocker issue, this one has some administrators scratching their head (and rightfully so). Microsoft says that updating the UEFI bios could help in some cases. However, if you have some models that are installing this update without any issues and the same models that are failing to install the update, the problem could be not with the UEFI bios version, but actually the TPM settings.
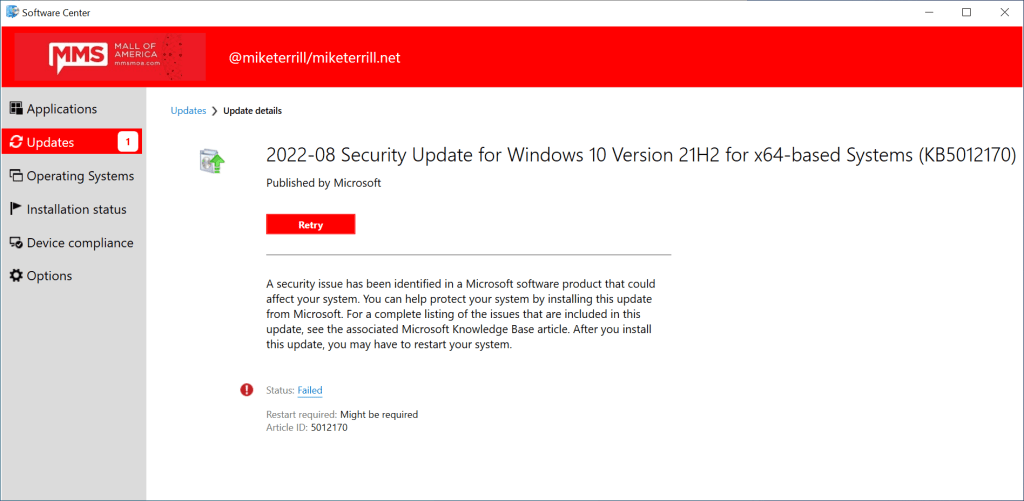
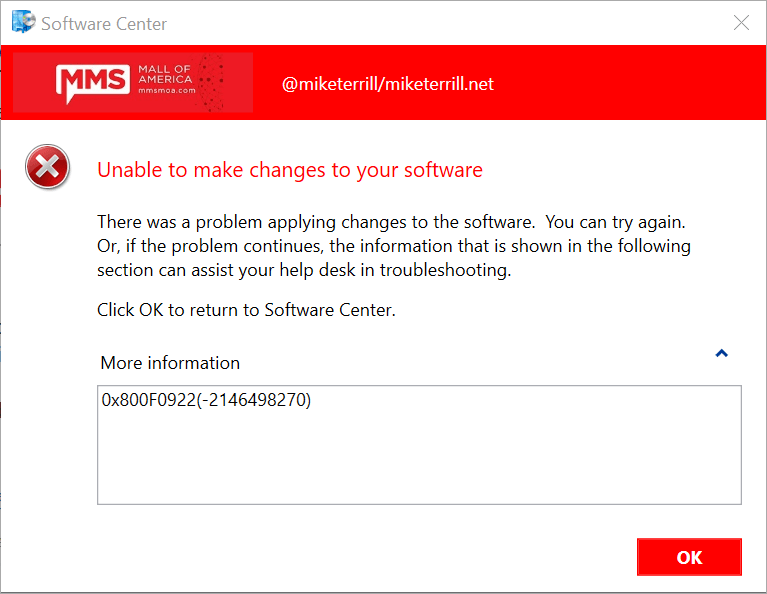
Running this update on a HP ProBook 445 G8 that I have in my lab, I was getting this exact error code:
Checking the TPM State configuration of this machine, I can see that the TPM State is set to Disable:
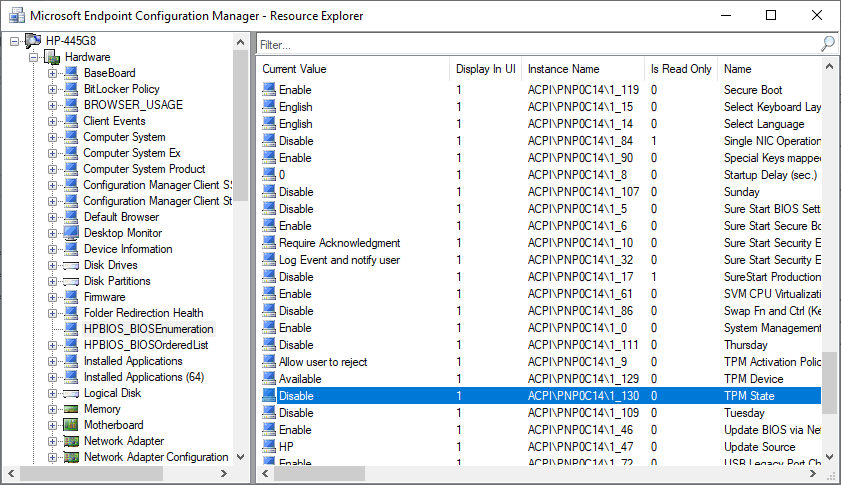
(See my post How to Inventory HP BIOS and UEFI Settings with ConfigMgr on how to get this data back via hardware inventory)
This also happens to be one of the settings that I talked about in my TPM Management – Getting Ready for Windows 11 session that I gave with Michael Niehaus at MMSMOA the past May:

This can be monitored and remediated using by creating a CI using the following PowerShell and along with TPM State, be sure to set the TPM Activation Policy to ‘No prompts’ so that the end user does not get prompted after the reboot:
#Discovery Script:
$SettingName = 'TPM State'
#-------------------------------------
$BIOSSetting = gwmi -class hp_biossetting -Namespace "root\hp\instrumentedbios" -Filter "Name='$SettingName'"
Write-Output $BIOSSetting.CurrentValue
#Remediation Script:
$SettingName = 'TPM State'
$Value = 'Enable' #Disable,Enable
$BIOSPW = 'Password1'
#-------------------------------------
$BIOS= gwmi -class hp_biossettinginterface -Namespace "root\hp\instrumentedbios"
$BIOSSetting = gwmi -class hp_biossetting -Namespace "root\hp\instrumentedbios"
If (($BIOSSetting | ?{ $_.Name -eq 'Setup Password' }).IsSet -eq 0)
{
$Result = $BIOS.SetBIOSSetting($SettingName,$Value)
}
elseif (($BIOSSetting | ?{ $_.Name -eq 'Setup Password' }).IsSet -eq 1)
{
$PW = "<utf-16/>$BIOSPW"
$Result = $BIOS.SetBIOSSetting($SettingName,$Value,$PW)
}
#Discovery Script:
$SettingName = 'TPM Activation Policy'
#-------------------------------------
$BIOSSetting = gwmi -class hp_biossetting -Namespace "root\hp\instrumentedbios" -Filter "Name='$SettingName'"
Write-Output $BIOSSetting.CurrentValue
Write-Output $BIOSSetting.PossibleValues
#Remediation Script:
$SettingName = 'TPM Activation Policy'
$Value = 'No prompts' #Disable,Enable
$BIOSPW = 'Password1'
#-------------------------------------
$BIOS= gwmi -class hp_biossettinginterface -Namespace "root\hp\instrumentedbios"
$BIOSSetting = gwmi -class hp_biossetting -Namespace "root\hp\instrumentedbios"
If (($BIOSSetting | ?{ $_.Name -eq 'Setup Password' }).IsSet -eq 0)
{
$Result = $BIOS.SetBIOSSetting($SettingName,$Value)
}
elseif (($BIOSSetting | ?{ $_.Name -eq 'Setup Password' }).IsSet -eq 1)
{
$PW = "<utf-16/>$BIOSPW"
$Result = $BIOS.SetBIOSSetting($SettingName,$Value,$PW)
}These will configure the following settings:

These settings do need a reboot before attempting the patch install again, but after the reboot, the patch should install just fine.
Originally posted on https://miketerrill.net/
Pingback: Master patch list for August 30, 2022 @ AskWoody
This article states: “Note I have never seen a windows patch turn on bitlocker.”
That is correct, this patch does not turn on BitLocker. In my article, I do not state that it does turn on BitLocker, so I am unsure of where the author of this article gets that impression. As I stated to a previous comment, I am pretty sure the laptop came with Win10 and he created a local account instead of using his MSFT account. When he upgraded it to Win11, that is when BitLocker got enabled but it had no where to store the recovery keys as he never signed on to it with his MSFT account.
” This happened to my father-in-law’s laptop and unfortunately the recovery key was not listed in his Microsoft account. His laptop was basically ransomwared without the ability to pay the ransom (luckily his son-in-law knows a thing or two about deploying Windows).”
Was the key in your Microsoft account? (If not, how could you recover?)
No, it wasn’t in his account. What I think happened was the laptop came installed with Win10 and he used a local account (instead of his MSFT account). When he upgraded to Win11, it automatically encrypted the drive but had no where to store the recovery keys…
Pingback: When Windows updating goes bad — the case of the problematic patch - IT News UG